74
business elite canada
H
AUGUST 2013
Security Operations Center
eSentire, Inc.
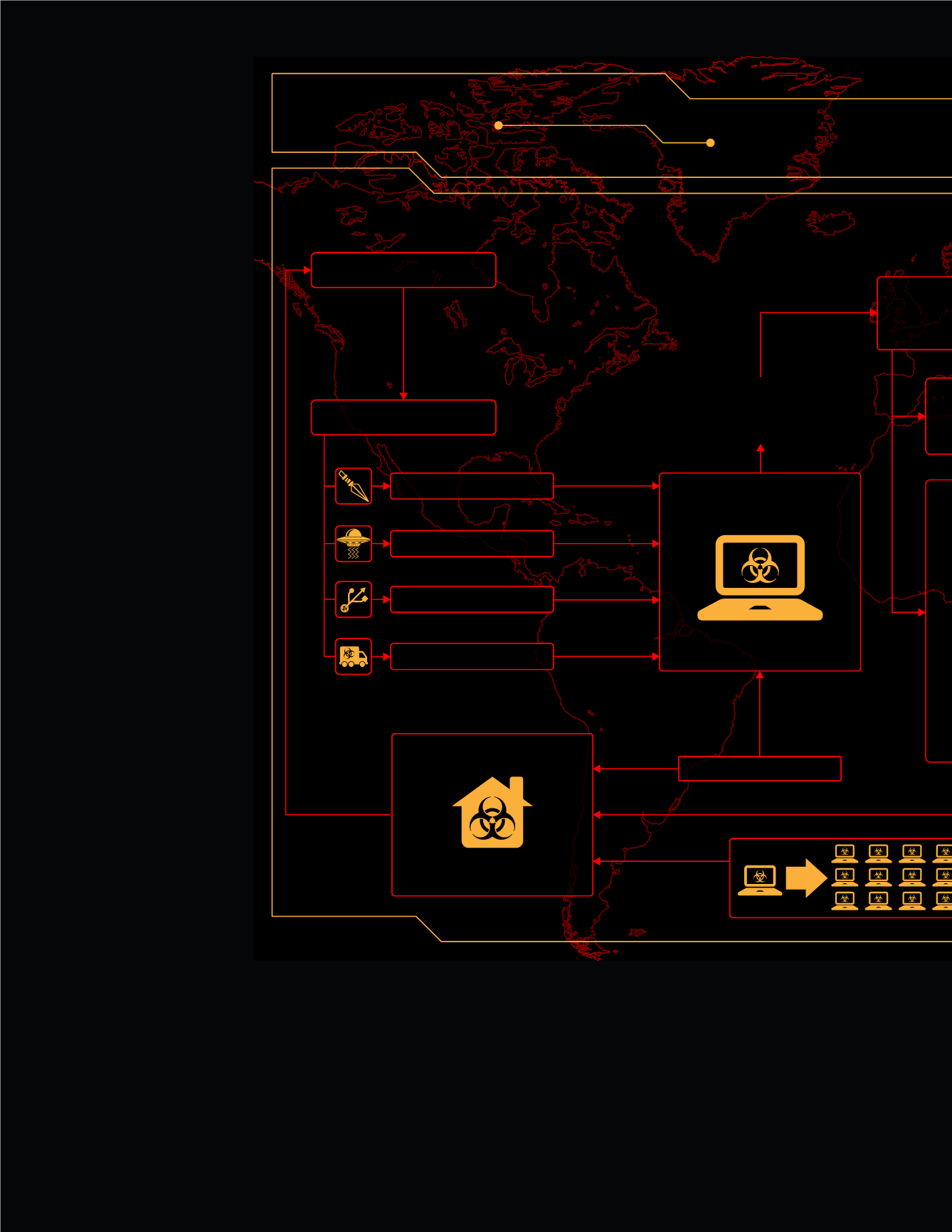
Anatomy of
SPEARPHISHING
M
N
M
LATER
‘Lear
ESTABLISH
C2 CHANNEL
MAINTAIN COVERT
REMOTE ACCESS
ESTABLISH
BEACH HEAD
Patient Zero
Escalation/
Extension/Expansion/
Further Penetration
Updates & Instructions
Vulnerability | Weak Credentials | SQL Injection
USB Drive | CDR | Laptop | Mobile Device | Wifi
Email Attachment| Malicious URL
EXTERNAL SCANS
PHYSICAL
Drive-by Download
OPPORTUNISTIC
ATTACKER
INFILTRATION
TIME
Unlike other security tech-
nologies on the market, eS-
entire’s main focus is protect-
ing an organization’s network
from the inside out. By initial-
ly assuming that the network
has been compromised, they
turn their focus to behaviors
that may suggest foul play.
There are four threat catego-
ries used in catching an at-
tack—insiders,
criminals,
nation states, and hackers. In-
siders are employees working
alongside criminals to retrieve
crucial information like bank
account information. Nation


